[Study Guide Review, Updated JULY, 2024] Certified Information Systems Auditor Cert code: CISA, Questions of the exam: 150, Minutes of the exam: 240, Correct to pass: 57%.
[Study Guide Review, Updated JUNE, 2024] Certified Information Systems Auditor Cert code: CISA, Questions of the exam: 150, Minutes of the exam: 240, Correct to pass: 57%.
[Study Guide Review, Updated MAY, 2024] Certified Information Systems Auditor Cert code: CISA, Questions of the exam: 150, Minutes of the exam: 240, Correct to pass: 57%.
[Study Guide Review, Updated MARCH, 2024] Certified Information Systems Auditor Cert code: CISA, Questions of the exam: 150, Minutes of the exam: 240, Correct to pass: 57%.
[Study Guide Review, Updated FEBRUARY, 2024] Certified Information Systems Auditor Cert code: CISA, Questions of the exam: 150, Minutes of the exam: 240, Correct to pass: 57%.
SOME NOTES ABOUT CERTIFIED INFORMATION SYSTEMS AUDITOR:
Certified Information Systems Auditor [CISA] is an important and mandatory certification on your path to becoming an expert in your field.
To get this certificate, you need to firmly and confidently grasp the content listed below. Then, you need to pass the exam directly on ISACA's system. This exam has a duration of 240 minutes, with 150 questions. You need to answer correctly at least 57% of the total questions on the exam.
Below are the contents that you need to grasp firmly and confidently before registering to take the exam on ISACA's system:
1. Information System Auditing Process Overview
1.1. IS Audit Standards, Guidelines and Codes of Ethics
1.2. Business Processes
1.3. Types of Controls
1.4. Risk-based Audit Planning
1.5. Types of Audits and Assessments
1.6. Audit Project Management
1.7. Sampling Methodology
1.8. Audit Evidence Collection Techniques
1.9. Data Analytics
1.10. Reporting and Communication Techniques
1.11. Quality Assurance and Improvement of the Audit Process
2. Governance and Management of IT Overview
2.1. IT Governance and IT Strategy
2.2. IT-related Frameworks
2.3. IT Standards, Policies and Procedures
2.4. Organizational Structure
2.5. Enterprise Architecture
2.6. Enterprise Risk Management
2.7. Maturity Models
2.8. Laws, Regulations and Industry Standards Affecting the
2.9. IT Resource Management
2.10. IT Service Provider Acquisition and Management
2.11. IT Performance Monitoring and Reporting
2.12. Quality Assurance and Quality Management of IT
3. Information Systems Acquisition, Development and Implementation
3.1. Project Governance and Management
3.2. Business Case and Feasibility Analysis
3.3. System Development Methodologies
3.4 Control Identification and Design
3.5. Testing Methodologies
3.6. Configuration and Release Management
3.7. System Migration, Infrastructure Deployment and Data Conversion
3.8. Post-implementation Review
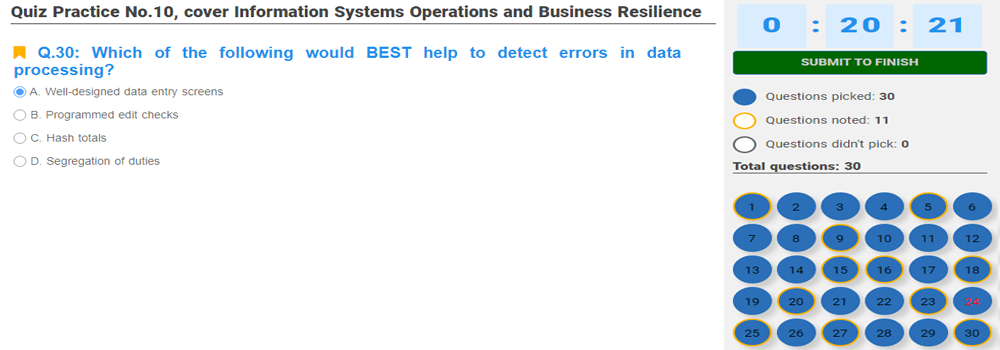
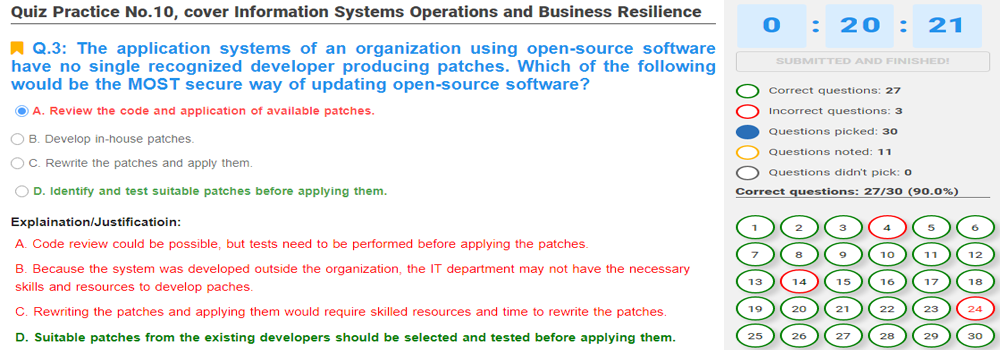
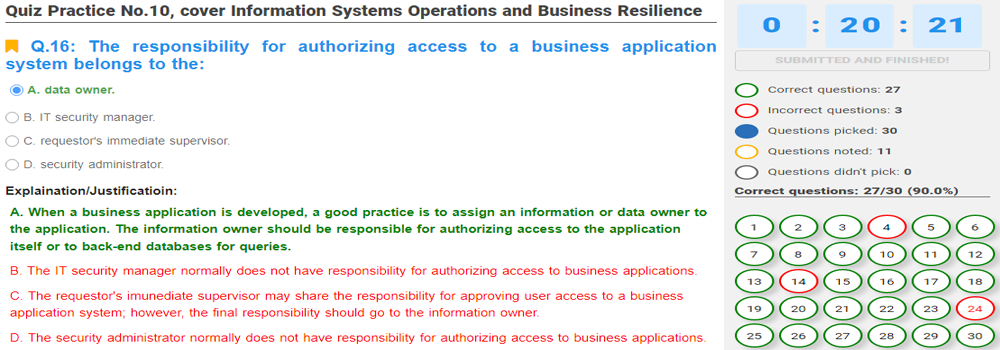
4. Information Systems Operations and Business Resilience
4.1. Common Technology Components
4.2. IT Asset Management
4.3. Job Scheduling and Production Process Automation
4.4. System Interfaces
4.5. End-user Computing
4.6. Data Governance
4.7. Systems Performance Management
4.8. Problem and Incident Management
4.9. Change, Configuration, Release and Patch Management
4.10. IT Service Level Management
4.11. Database Management
4.12. Business Impact Analysis
4.13. System Resiliency
4.14. Data Backup, Storage and Restoration
4.15. Business Continuity Plan
4.16. Disaster Recovery Plans
5. Protection of Information Assets
5.1. Information Asset Security Frameworks, Standards and Guidelines
5.2. Privacy Principles
5.3. Physical Access and Environmental Controls
5.4. Identity and Access Management
5.5. Network and End-point Security
5.6. Data Classification
5.7. Data Encryption and Encryption-related Techniques
5.8. Public Key Infrastructure
5.9. Web-based Communication Technologies
5.10. Virtualized Environments
5.11. Mobile, Wireless and Internet-of-things Devices
5.12. Security Awareness Training and Programs
5.13. Information System Attack Methods and Techniques
5.14. Security Testing Tools and Techniques
5.15. Security Monitoring Tools tand Techniques
5.16. Incident Response Management
5.17. Evidence Collection and Forensics
GOODLUCK TO YOU!!!